Part 1: Concepts for SSL and Oracle Certification Authority (OCA)
Part 2: SSL Configuration with OCA and Oracle Wallet Manager (OWM)
Part 3: OHS (Oracle HTTP Server) Configuration for SSL
Part 4: Additional topics for SSL with OracleAS 10g such as EBS
Concepts for SSL and Oracle 10gAS PKI
The Oracle Public Key Infrastructure (PKI) is the big picture for managing certificates within Oracle Fusion Middleware components. PKI consists of the following items:
- Secure Sockets Layer (SSL)
- Oracle Wallet Manager (OWM), containers and wallets
- the Oracle Internet Directory (OID) and Oracle 10g Application Server Single Sign On (SSO)
We have discussed most of these components already for OID and SSO. However, before we manage to discuss the details for SSL configuration with Oracle 10gAS, we need to first understand how to configure the Oracle Certificate Authority (OCA) and Oracle Wallet Manager (OWM).
Understanding Certificates with Oracle PKI Components for 10gAS
Digital certificates are electronic documents that establish security credentials for transactions within Oracle 10gAS including Oracle 10g Portal, Reports, and Discoverer applications. Each certificate contains the username and digital signature from the issuing certificate authority (CA). We have a few different types of certificates:
- Client based certificates: also known as end-entity certificates which contain personal or user certificates
- Web server certificates contain server side digital signature for secure web communications between servers.
- root authority certificates are self signed certificates which form the base or root of a certificate authority (CA).
What is a certificate authority (CA) ? A certificate authority is a third party such as Verisign that provides the verified credentials for an organization and issues the security certificates used for all SSL connections. This CA performs the authentication of the user's certificate identity so that it is trusted within the 10g Application server environment. Oracle 10gAS provides a utility called the Oracle Certificate Authority (OCA) which administers and manages these certificates. After the certificate is available it needs a storage place for safe keeping and reference during 10gAS processing of transactions. Here is where the Oracle Wallet Manager (OWM) utility comes into play. We have two choices where to store these trusted certificates: in an LDAP directory system or a wallet manager. The Oracle Wallet Manager (OWM) allows us to store these certificates in a repository schema located in the 10gAS Infrastructure database for safe keeping. We can use the PKCS #12 (Personal Information Exchange Syntax) standard if we so wish as part of the certification process. The Oracle Wallet Manager (OWM) allows us to manage the security credentials for clients and servers.
How Does SSL Work?
The SSL process operates in the following series of steps to provide secure communication between the user's client and Oracle 10g Application Server.
1. An end user connects to the 10g Application Server and submits a request on the SSL port via HTTPS protocol.
2. The server verifies the user's identity by signing the certificate and sending it back to the client
3. The client end user will use the server public key to verify that the owner of the certificate is indeed the same user who signed it. If the certificate authority (CA) credentials are unknown, the end user client browser replies that the certificate was issued by an unknown CA.
4. The user manually verifies that the site certificate has been issued by a trusted authority ie) Verisign and generates a encypted token using the server's public key.
5. The certificate is sent back to the server and SSL performs a handshake operation based on the cipher in the public key. If the session keys match, the certificate is accepted and the end user is able to access the Oracle 10g Application server applicatons via SSL.
The Oracle Certificate Authority (OCA) verifies all details of the operations for SSL with the SSO and OID servers during this process. Now that we have provided an introduction to SSL and Oracle PKI security, lets present some hands on examples of how to configure certificates for SSL with the Oracle Certificate Authority (OCA).
Setup and Configuration for Oracle Certificate Authority (OCA)
By default, after installing the Oracle 10gAS infrastructure components for Oracle 10g Application Server, the OCA is not started. As such, we need to start and verify the processes for the OCA.
By default, the OCA configuration files live under the $ORACLE_HOME/oca/conf directory for the 10gAS infrastructure.
We need to startup the OCA by using the ocactl utility located under $ORACLE_HOME/oca/bin. Once we start the OCA processes by executing the ocactl start command, we are ready to configure the certificates for Oracle 10gAS.
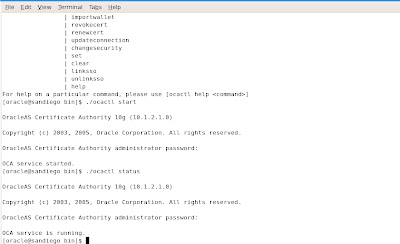
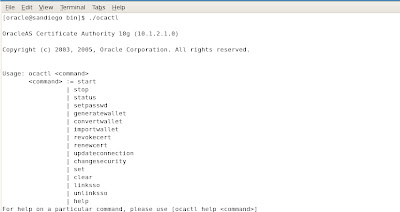
To get help on using the ocactl commands, we have the following example:
The oca.xml file contains the main settings for the configuration of the OCA for Oracle 10g Application server as shown in the following example.
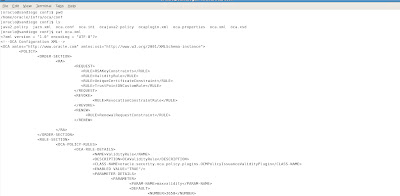
You can edit the file with any XML editor utility.
Since OCA relies on wallets to store the various PKI credentials and password storage area for passwords. The OCA requires the certificate authority (CA) signing wallet as well as the CA SSL wallet. The CA signing wallet is created by the Oracle 10gAS installer or can be imported from another CA to setup a custom CA structure. The new wallet along with the signed key and certificate are signed by the new CA. The SSL certificate authority wallet is created by the 10gAS installer when you install 10g Application Server components for the Infrastructure. It contains the SSL certificate and private key for the SSL server that hosts the OCA. This SSL wallet can also be imported from another certificate authority (CA) or managed by the Oracle Wallet Manager (OWM) utility.
To access the OCA interface from within Oracle 10g Application Server, we can navigate to the 10gAS home page for OCA based on https://server:
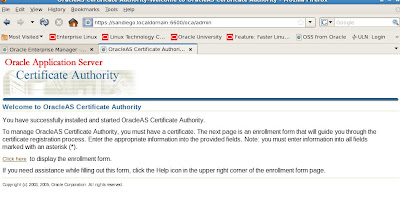
We can also check the details from the main 10gAS application server infrastructure page for OCA operations.

Now lets return to the main OCA interface that we discussed earlier. The first step for configuration after we have started the OCA processes with 10g Application Server is to setup the enrollment process for certificates.

The fields with asterisks are required by OCA. Here we use ocawebadmin as our user with ABC
for the organization. We also have options below to setup the certificate information.
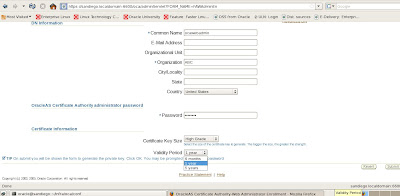
We can set the time period for the certificate from 6months to 5 years. We also have an option to set the certificate key size to either high grade or medium grade based on our security and encryption policy standards. We finalize our setup and click the submit button which will process our new certificate details as shown below.
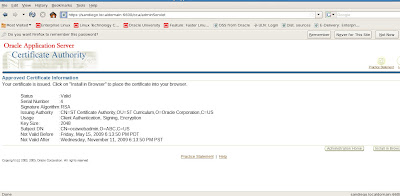
Now that we have our OCA certificate for administration tasks, we need to import it into our web browser! To do so, we choose the option below to install in browser.
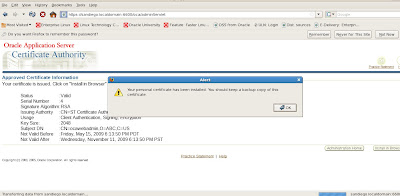
Once we have successfully added the new certificate to our browser, we save the backup copy and return to our main OCA administration page to verify all certificates and their status. Since this was a test certificate that we used previously, OCA rejected our new certificate request. So we will need to revoke all certificates by using the ocactl revokecert command. In the next post, we will cover these tasks in more detail to complete our coverage for SSL with Oracle 10g Application Server. In a nutshell the reason why this failed was because the certificate also needs to exist in the Oracle Wallet Manager (OWM). If the certificate cannot be found by OWM, it will be rejected by the OCA. So we will need to clear out all certificate requests and recreate a new wallet and certificate for SSL to be used by the Oracle 10g Application Server. We conclude this introduction to SSL configuration with a summary display of the main OCA administration page for certificate management.
The first general pages provides us with options to manage and configure certificates and certificate requests.
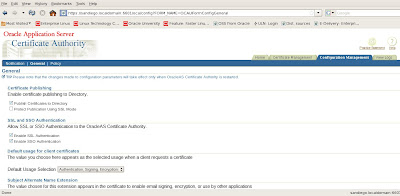
When we first access the general tab, the certificate will popup to ask us if we trust it or not as confirmation.
We have many options here to configure and publish the certificate with SSL. We can enable or disable SSL and/or SSO authentication for our certificates as well as configure directory settings for the LDAP OID server. We also have a Notification tab to setup our SMTP server for emailing alerts and messages to the OCA administrator.
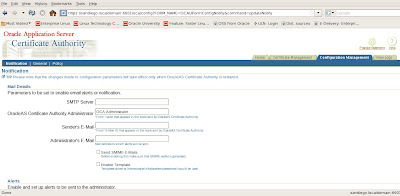
If we need to change policy settings for managing our certificates, we navigate to the Policy tab for the OCA Administration web console.
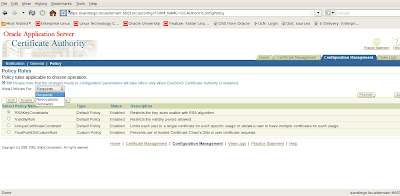
We can set policy rules for certificates based on requests, revocations or renewals. Under the Certificate Management tasks menu, we can also update our Certificate Revocation List (CRL).
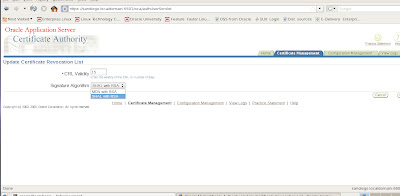
We have menu options to enter the number of days to keep the certificate revocation list valid in days (CRL Validity)
as well as the Signature Algorithm choice between SHA1 with RSA or MD5 with RSA.
On a final note for our introduction to SSL with Oracle 10gAS, there is an option to customize the certification practice statement issued by the OCA within Oracle 10g Application Server applications. By editing the ocaadmin_cs_practicestmt.html file located under $ORACLE_HOME/j2ee/oca/applications/oca/helpsets/oca_practice_stmt, IT security administrators can have a department message issued by Corporate IT security as part of the messaging system.
We will conclude our discussion of SSL for Oracle 10gAS in our next post by explaining the setup and configuration of the Oracle Wallet Manager (OWM) with the Oracle Certificate Authority (OCA) for SSL.










2 comments:
Thanks for this article. This article extends to provide added information about a oracle server authenticity. I bought the SSL certificate from the tucktail.
Great post Ben. Unfortunately for me I was a bit miffed on how to install ssl certificate for my new retail website. I got SSL 247 to sort it all out for me and now any customers that come to my site can shop securely.
Post a Comment