In the first two parts, we illustrated how to configure the core functions for Identity Management (IdM) with Oracle 10gAS Fusion Middleware. In this section, we will explain how to setup the Oracle HTTP Server or OHS for SSL with Oracle 10g Application Server. OHS is Oracle's implementation of the Apache 1.3 webserver which is an integral component of the Oracle Fusion Middleware technology. In addition to playing a pivotal role in the Oracle 10gAS, OHS is a key ingredient in the Oracle Applications EBS technology stack. With SSL, we can secure HTTP communication between the user's web browser and OHS web server. OHS uses the mod_ossl module or plugin to implement SSL within the web server which fully supports SSL 3.0 standards.
We also have a useful SSL configuration tool (SSLConfigTool) that we will see later on in our discussion which automates many of the steps for us to secure the HTTP protocol with OHS. The SSLConfigTool is located under $ORACLE_HOME/bin directory.
How to Configure SSL with OHS
To configure OHS with SSL, we need to modify the httpd.conf configuration file for OHS to tell Apache 1.3 ahem, OHS server
that it will use SSL for security settings. The httpd.conf file is located under the $ORACLE_HOME/Apache/Apache/conf directory.
The following parameters are key to understanding SSL configurations with OHS:
- ServerName the server which will be enabled for SSL
- SSLWallet File directory path location for the server wallet
- SSLEngine setting to either enable or disable SSL
- SSLVerifyClient verification type for client certificates
we have three options here: none which means SSL without certificates
Optional- only user server certificate
Require: use both server and client certificates
Once we have configured OHS for SSL, we can access the OHS server from secure HTTPS protocol
from the host with https://hostname.domain:4443
Oracle OHS uses the port 4443 as the default port for SSL communications
Now, lets take a look at our current OHS httpd.conf configuration file settings
##
## httpd.conf -- Apache HTTP server configuration file
##
#
# Based upon the NCSA server configuration files originally by Rob McCool.
#
# This is the main Apache server configuration file. It contains the
# configuration directives that give the server its instructions.
# See
# the directives.
#
# Do NOT simply read the instructions in here without understanding
# what they do. They're here only as hints or reminders. If you are unsure
# consult the online docs. You have been warned.
#
# After this file is processed, the server will look for and process
# /home/oracle/infra/Apache/Apache/conf/srm.conf and then /home/oracle/infra/Apache/Apache/conf/access.conf
# unless you have overridden these with ResourceConfig and/or
# AccessConfig directives here.
#
# The configuration directives are grouped into three basic sections:
# 1. Directives that control the operation of the Apache server process as a
# whole (the 'global environment').
# 2. Directives that define the parameters of the 'main' or 'default' server,
# which responds to requests that aren't handled by a virtual host.
# These directives also provide default values for the settings
### Section 1: Global Environment
#
# The directives in this section affect the overall operation of Apache,
# such as the number of concurrent requests it can handle or where it
# can find its configuration files.
#
#
# ServerType is either inetd, or standalone. Inetd mode is only supported on
# Unix platforms.
#
ServerType standalone
#
# ServerRoot: The top of the directory tree under which the server's
# configuration, error, and log files are kept.
#
# NOTE! If you intend to place this on an NFS (or otherwise network)
# mounted filesystem then please read the LockFile documentation
# (available at
# you will save yourself a lot of trouble.
#
# Do NOT add a slash at the end of the directory path.
#
ServerRoot "/home/oracle/infra/Apache/Apache"
#
# The LockFile directive sets the path to the lockfile used when Apache
# is compiled with either USE_FCNTL_SERIALIZED_ACCEPT or
# USE_FLOCK_SERIALIZED_ACCEPT. This directive should normally be left at
# Port: The port to which the standalone server listens. For
# ports < 1024, you will need httpd to be run as root initially.
#
# This port is used when starting without SSL
Port 7777
Listen 7777
#
# If you wish httpd to run as a different user or group, you must run
# httpd as root initially and it will switch.
#
# User/Group: The name (or #number) of the user/group to run httpd as.
# . On SCO (ODT 3) use "User nouser" and "Group nogroup".
# . On HPUX you may not be able to use shared memory as nobody, and the
# suggested workaround is to create a user www and use that user.
# NOTE that some kernels refuse to setgid(Group) or semctl(IPC_SET)
# when the value of (unsigned)Group is above 60000;
# don't use Group nobody on these systems!
#
User oracle
Group oinstall
#
ServerName sandiego.localdomain
#
# DocumentRoot: The directory out of which you will serve your
# documents. By default, all requests are taken from this directory, but
# symbolic links and aliases may be used to point to other locations.
#
DocumentRoot "/home/oracle/infra/Apache/Apache/htdocs"
#
# Each directory to which Apache has access, can be configured with respect
# to which services and features are allowed and/or disabled in that
# directory (and its subdirectories).
#
# First, we configure the "default" to be a very restrictive set of
# permissions.
#
Options FollowSymLinks MultiViews
AllowOverride None
We also need to update settings for the Oracle Process Manager and Notification (OPMN) for our Portal 10gAS instance
by changing settings for the opmn.xml configuration file located under the $PORTAL_HOME/opmn/conf directory. We can either edit this configuration file for Portal directly or more conveniently, to use the Oracle 10gAS Application Server Control for the Portal instance under Process Management tab. Below is our sample opmn.xml config file for Portal:
Of note here for our purposes, is that we need to enable SSL communication for the OHS HTTP Apache 1.3.x web server. By default, SSL is NOT enabled! So we need to find the section in the opmn.xml file that references the HTTP server. Below is the relevant section:
ias-component id="HTTP_Server"
process-type id="HTTP_Server" module-id="OHS"
module-data
category id="start-parameters"
data id="start-mode" value="ssl-disabled"
We need to change this to "ssl-enabled" and resync OHS to allow SSL settings to take affect.
I prefer to use Application Server control because if we edit the opmn.xml file directly, we need to resync it manually which can be a pain. Application Control Server does this automatically for us. Under the main Portal instance page for 10gAS, we navigate to Process Management as shown below
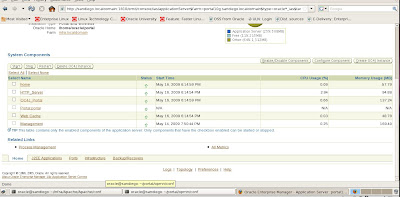
This brings us directly to the editor for the opmn.xml file and we update it to enable the SSL option

We apply the changes.
Now we need to verify that our certificates can be accepted and then apply final configuration changes to the OHS httpd.conf file to ensure SSL communications function correctly. First, we need to navigate to the Oracle Certificate Authority (OCA) user page. We also need to clear out our web browser and remove old certificates since we are using the same server for our testing purposes.
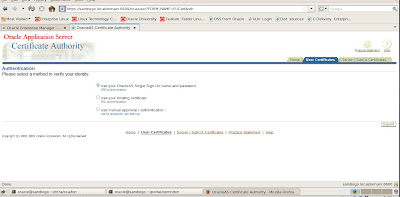
We use our administrator account and password to login via SSO
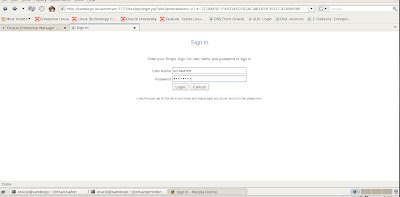
Once we login, we can view certificates that we created earlier
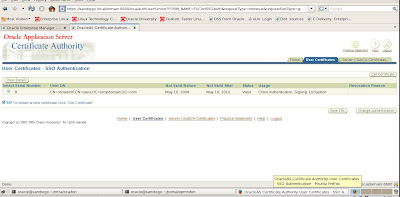
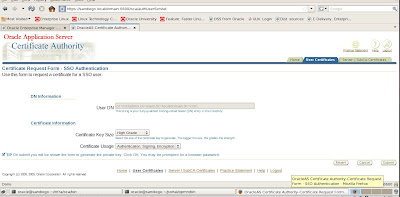
We choose to get our certificate by choosing the option Get Certificate which will be used for future SSL communications
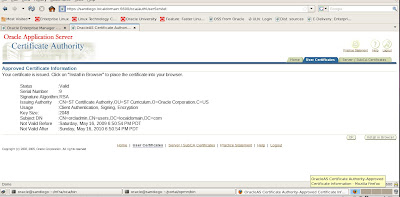
Details for the certificates are shown below.
Now we need to add the directives to the Portal Instance OHS web server to complete our setup for enabling SSL with Oracle
10g Application Server.
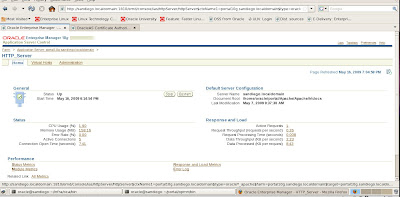
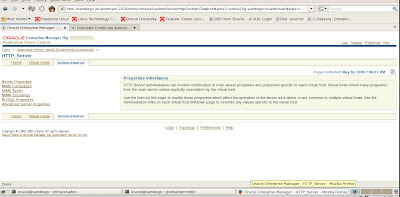
To complete our SSL tasks for OHS, we need to select Advanced Server Properties tab in the HTTP Server administration web page.
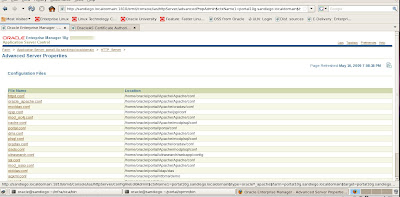
Since the httpd.conf configuration file for OHS is what need to modify to complete our SSL setup for Oracle HTTP Server, we click on the link.
We need to add a couple of directives to our Apache (OHS) httpd.conf configuration file to enable SSL.
SSLVerifyClient require
We then click the Apply button and OHS will need to restart the web server to apply our changes for SSL. Be careful editing this file since any typos will cause the OHS web server to fail to restart.
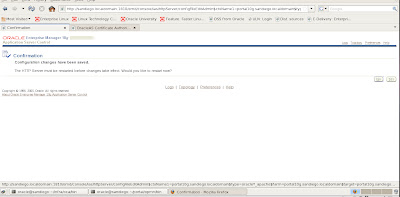
Now hopefully, our Apache web server OHS restarts with the enabled SSL changes.
A good reference for Apache and OHS since OHS really is Oracle's rebranded version of the Apache 1.3 web server is to consult the Apache main site http://apache.org
For reference on the Apache and OHS SSL directives the link
http://httpd.apache.org/docs/2.2/mod/mod_ssl.html has excellent supplemental details.










No comments:
Post a Comment