Dear readers,
We will provide some tips on how to integrate key features of Oracle 10gAS with the R12 EBS Applications suite.
First, we will provide a quick summary of the architecture that exists within Oracle E-Business Suite Release 12 in terms of
Oracle 10gAS.
Oracle Metalink Note #
415007.1 is a FAQ that provides a useful summary of ways to integrate the Oracle R12 EBS Suite with Oracle 10g Application Server. Even though Oracle Weblogic is the heir apparent for future Application Server/Fusion Middleware directions as evidenced by the SOA suite products, fact is that Oracle 10g Application Server is the core middleware technology at work for Oracle R12 Applications E-Business Suite.
One key difference between a stand alone Oracle 10g Application Server environment versus R12 EBS is that the
Oracle 10gAS Infrastructure is NOT SUPPORTED in the Release 12 of Oracle E-Business Suite for Oracle 12i Applications. Oracle Metalink Note
251627.1tells further details on how to workaround this issue.
Oracle Application Server 10g integration with Oracle EBS R12
Oracle EBS R12 uses many of the components that exist in Oracle 10g Application Server. For Oracle R12, these include:
- OHS- the Oracle HTTP Server (Apache 1.3)
- PL/SQL
- Forms Server
- Reports Server
- OC4J- Oracle Containers for J2EE
What versions of Oracle Application Server 10g can be used with Oracle E-Business Suite Release 12?
Oracle EB R12 has an Oracle 10g application server instance (10.1.2) that runs the Forms and Reports Services. In addition to this application server instance, we also have a secondary application server instance (10.1.3) which is used to run the OC4J instance. By default, when you install Oracle EBS R12, these 10gAS instances are installed and created by the R12 Rapid Install process.
Oracle R12 EBS supports the following Oracle Application Server 10g services:
Single Sign-On 10g (10.1.2.0.2)
Oracle Internet Directory 10g (10.1.2.0.2)
Portal 10g (10.1.4)
Discoverer 10g (10.1.2.0.2)
Web Cache 10g (10.1.2.0.2)
Oracle Business Integration 10g (10.1.3)
Oracle BPEL Process Manager 10g (10.1.3)
A complete discussion on how to setup and configure all of these products with EBS R12 would require a book in itself so I will kindly refer you to the Oracle EBS R12 Tech Stack Roadmap guide available in Oracle Metalink Note #
380482.1 Our main discussion will now shift to SSL and R12 EBS for Oracle 10g Application Server.
I have two homework assignments for you, besides the previous Metalink notes, I have another humble request. Either download or order the 29 DVDs for R12 EBS. Install a new test instance single tier for R12. You can do this at low cost with an external 250Gb portable drive, low cost laptop with 2-4Gb RAM, and VMWare. I built my R12 EBS test environment on Oracle Enterprise Linux for under $1000 and this included all softwares which are available from the Oracle Edelivery store (about $125 for non-commercial usage trial learning versions). Second, the following Metalink Notes are germane to our discussion for SSL, OID, and SSO with R12 EBS and Oracle 10g Application Server.
Note 376811.1, Integrating Oracle E-Business Suite Release 12 with Oracle Internet Directory and Oracle Single Sign-On
Note 403537.1, Best Practices for Securing Oracle E-Business Suite Release 12
Note 376694.1, Using the Oracle Wallet Manager Command Line Interface with Oracle E-Business Suite Release 12
Note 376700.1, Enabling SSL in Oracle Applications Release 12
Note 380490.1, Oracle E-Business Suite Release 12 Configuration in a DMZ
Since we already covered OID and SSO in great detail, for now, I will focus on SSL and R12 EBS for Oracle 10g Application Server.
SSL and Oracle 12i (Release 12) Applications
For us, the biggest change for using the Secure Sockets Layer (SSL) in terms of R12 and Oracle 10gAS is the use of mod_ossl module (plugin) for the Oracle HTTP Server (OHS). Both mod_ssl and mod_ossl enable strong cryptography for OHS (Apache 1.3). However, the key difference to note here is that mod_ossl is based on Oracle's implementation of SSL which supports SSL 3.
Oracle R12 EBS manages SSL certificates from the Oracle Wallet Manager (OWM) which we saw earlier in addition, we can also manage the wallets for SSL certificates with the new ORAPKI command line interface (CLI). The good news here for Oracle EBS, is that R12 now uses the Forms Listener Servlet, so we do not have a Forms server that existed in earlier releases of EBS such as 11i. This means that a separate certificate is no longer needed for Forms. Forms share the same wallet as the Oracle HTTP Server (OHS). However, I would like to point out an important caveat or gotcha. We no longer can use the Forms Server listener with the ConnectMode=https. This is no longer supported in Release 12i for Oracle E-Business Applications with R12. For R12 EBS, ConnectMode=https will only work with the JInitiator that contains the Oracle SSL libraries. Release 12 uses Sun's Java Plugin so in case you need to use https for the forms communication layer, it is imperative that you use the servlet architecture.
Middle Tier Configuration Steps to Enable SSL with Oracle R12 Applications
By default the location for the Oracle wallet in R12 is under
$INST_TOP/certs/Apache. This directory contains a wallet with demo certificates. If you wish to use these certificates for testing start with Step 8 below to configure SSL, and then do Steps 1 through 7 when you are ready to switch to real certificates.
The demo certificates are not secure and should never be used in a production environment.
The main steps for setting up SSL on the Middle Tier are:
1. Set Your Environment.
2. Create a wallet.
3. Create a Certificate Request.
4. Submit the Certificate Request to a Certifying Authority.
5. Import your Server Certificate to the Wallet.
6. Copy the Apache Wallet to the OPMN Wallet.
7. Update the JDK Cacerts File.
8. Update the Context File.
9. Run Autoconfig.
10. Restart the middle tier services.
We will use the Oracle Wallet Manager (OWM) to configure SSL and certificates.
An optional method is to use the CLI (Command Line Interface) with Oracle Wallet Manager for R12. To do so, I refer you to Oracle Metalink Note#
376694.1: Using the Oracle Wallet Manager Command Line Interface in Release 12. Ready for some real fun? OK! Great, lets configure SSL for Oracle E-Business Release 12i.
Set the R12 Environment
Login as applmgr or the OS user who owns the Apps Tier for your Oracle 12i EBS environment.
Source the environment file
[applmgr@ebs scripts]$ whoami
applmgr
[applmgr@ebs scripts]$ cd $APPL_TOP
[applmgr@ebs appl]$ . APPSPROD_ebs.env
[applmgr@ebs appl]$
Create the Wallet
Navigate to $INST_TOP/certs/Apache directory to create the new wallet.
[applmgr@ebs appl]$ cd $INST_TOP/certs/Apache
[applmgr@ebs Apache]$ pwd
/d01/app/oracle/inst/apps/PROD_ebs/certs/Apache
[applmgr@ebs Apache]$ ls
cwallet.sso ewallet.p12
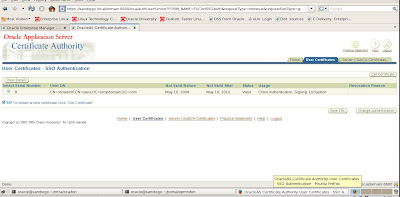
You should see the demo wallets that Rapid Install created after R12 was installed as shown above. Start the OWM (Oracle Wallet Manager) as shown in the figure example listed below.
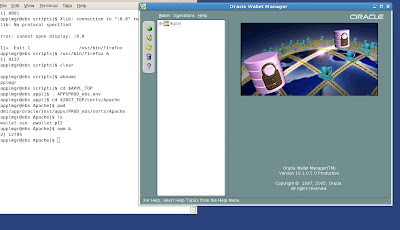
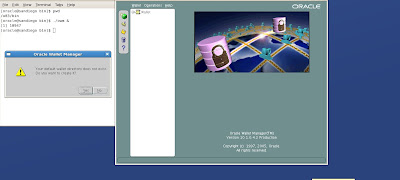
Select the option Wallet-> New
It will prompt you with “Your default wallet directory doesn't exist. Do you wish to create it now?” Choose No.
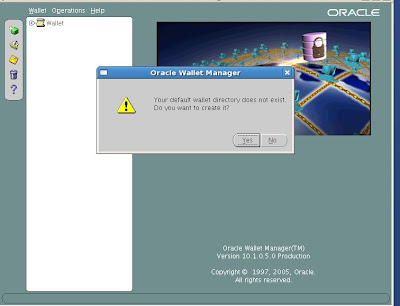
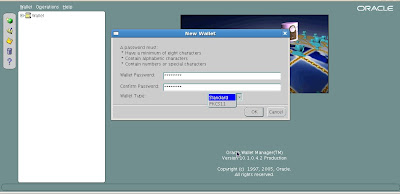
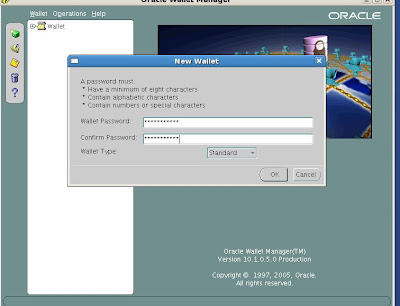
The new wallet screen will now prompt you to enter a password for your wallet.
Enter the password
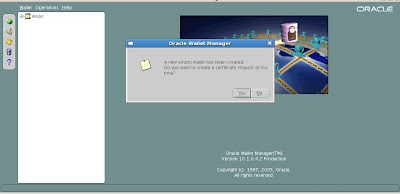
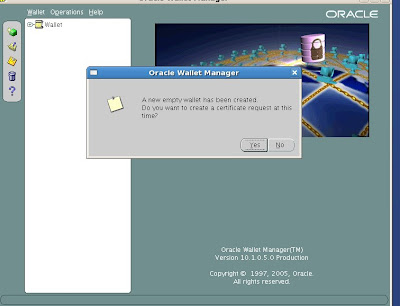
The new empty wallet is created. We do need to create the new certificate request so choose yes.
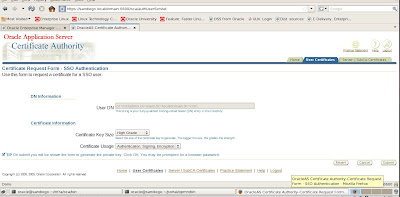
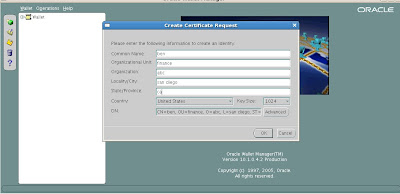
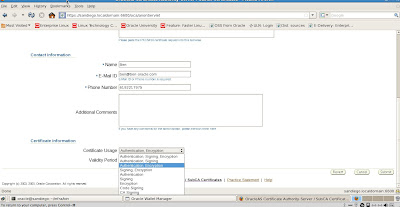
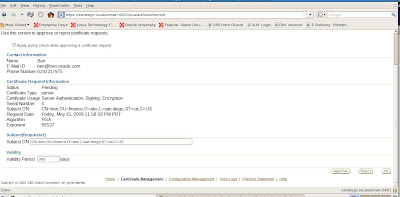
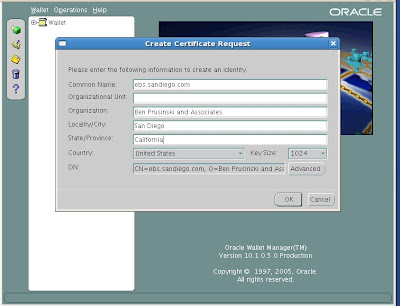
Common Name: is the name of your server including the domain.
Organizational Unit: (optional) The unit within your organization.
Organization: is the name of your organization.
Locality/City: is your locality or city.
State/Province: is the full name of your State or Province - do not abbreviate.
Select your Country from the drop down list.
Click OK.
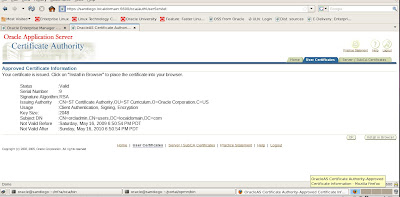
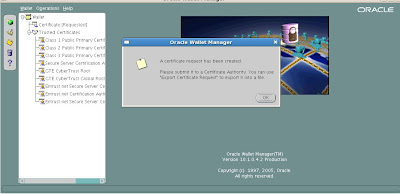
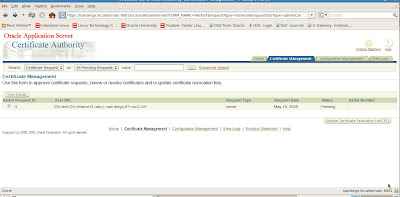
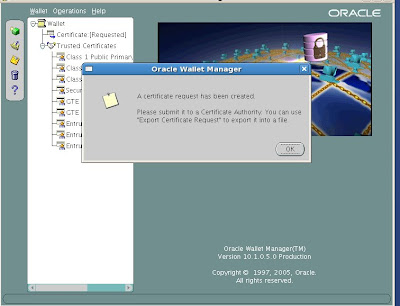 Submit the Certificate Request to a Certifying Authority (CA)
Submit the Certificate Request to a Certifying Authority (CA)
We see our new wallet details below.
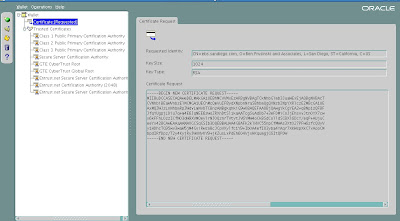
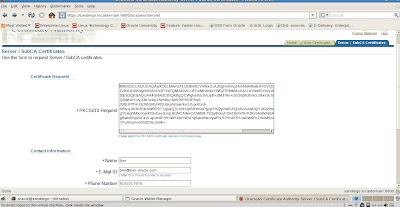
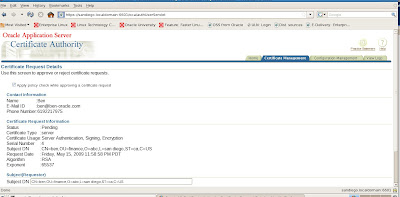
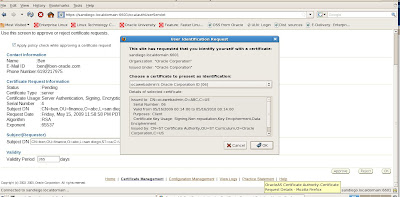
Now that we have our new wallet, we will need to export the Certificate Request and then submit it to a Certifying Authority (CA). Here are the steps.
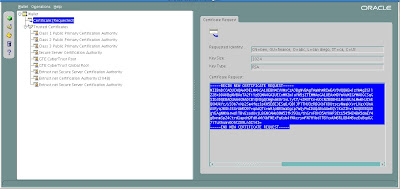
Click on Certificate [Requested] to Highlight it.
From the menu click Operations -> Export Certificate Request
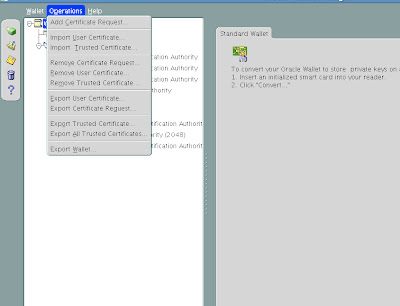
Save the file as server.csr
From the menu click Wallet and then click Save.

Change the Directory to the fully qualified wallet directory which in our case would be
/d01/app/oracle/inst/apps/PROD_ebs/certs/Apache
Click the OK button.
From the menu click Wallet and check the Auto Login box.
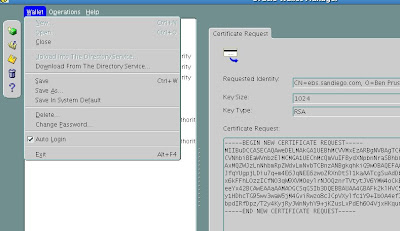
We will need to use the password whenever we open the wallet with Oracle Wallet Manager or if we ever need to perform operations on the wallet. Auto login allows for simplified maintenance tasks in the future.
Exit out of OWM
Our wallet directory now contains the following files:
[applmgr@ebs Apache]$ whoami;pwd;ls
applmgr
/d01/app/oracle/inst/apps/PROD_ebs/certs/Apache
cwallet.sso ewallet.p12 server.csr
Import Server Certificate to the Wallet.
Once we have received our Server Certificate the Certifying Authority (CA) we need to import it into our wallet. We copy the certificate to server.crt in the wallet directory by either using ftp or copy and paste into a server.crt file.
We use OWM (Oracle Wallet Manager) to perform this task.
Modify Wallet for Oracle Process and Notification Manager (OPMN)
Oracle Applications R12 Rapid Install creates a default "demo" type opmn wallet in the $INST_TOP/certs/opmn directory that is available for basic SSL testing. Now that the Apache wallet has been created for us, we need to to use these same certificates for opmn. We need to perform the the following steps to backup and copy the wallets:
Navigate to the $INST_TOP/certs/opmn directory.
Create a new directory named BAK
Move the ewallet.p12 and cwallet.sso files to the BAK directory just created.
Copy the ewallet.p12 and cwallet.sso files from the $INST_TOP/certs/Apache directory to the $INST_TOP/certs/opmn directory.
[applmgr@ebs Apache]$ cd $INST_TOP/certs/opmn
[applmgr@ebs opmn]$ mkdir BAK
[applmgr@ebs opmn]$ cp /d01/app/oracle/inst/apps/PROD_ebs/certs/Apache/e* cw* $INST_TOP/certs/opmn/BAK
[applmgr@ebs BAK]$ pwd
/d01/app/oracle/inst/apps/PROD_ebs/certs/opmn/BAK
[applmgr@ebs BAK]$ ls
cwallet.sso ewallet.p12
Make SSL Updates for R12 EBS Context File.
Now we need to update our R12 EBS Context file variables to account for SSL configuration.
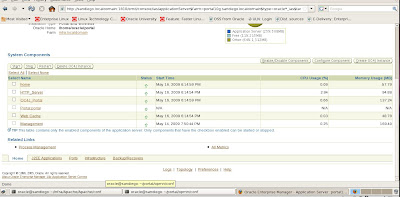
To do so, we need to use the Oracle Applications Manager (OAM) Context Editor to change the SSL related variables as shown in the following screenshots.
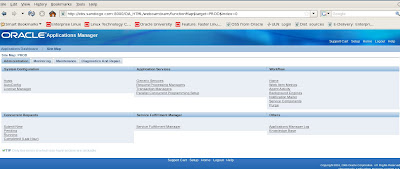
We choose AutoConfig under System Configuration on the Oracle 12i Applications Manager (OAM) interface to access our context files.
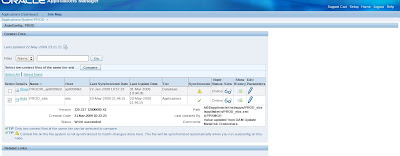
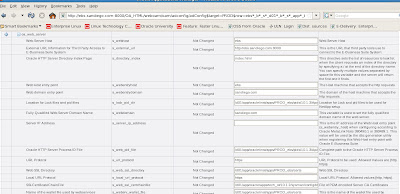
Now we need to edit the Context file for Apps Tier to enable SSL for R12 E-Business environment.
Change variables for s_url_protocol from http to https for SSL and make sure to set the s_webssl_port to 4433 which is the default SSL port. Below is an example.
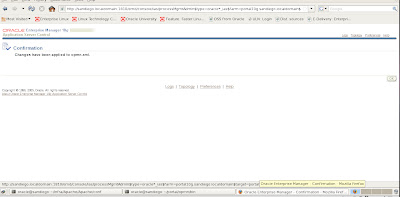
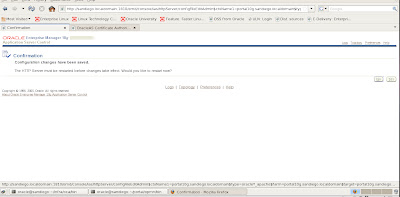
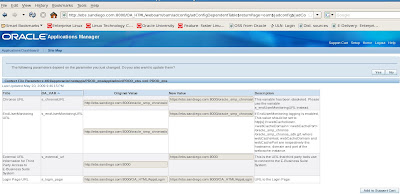 Finalize changes for R12 EBS and SSL Configuration - Autoconfig
Finalize changes for R12 EBS and SSL Configuration - Autoconfig
Now we need to run the Autoconfig utility to have our changes made to our R12 context file for SSL. We do this by executing the adautocfg.sh script located in the Middle Tier (Apps Tier) under the $ADMIN_SCRIPTS_HOME directory.
$ cd $ADMIN_SCRIPTS_HOME
[applmgr@ebs scripts]$ ls
adalnctl.sh adcmctl.sh adformsrvctl.sh adopmnctl.sh adstrtal.sh java.sh L308828.log sqlnet.log
adapcctl.sh adexecsql.pl adoacorectl.sh adpreclone.pl gsmstart.sh jtffmctl.sh mwactl.sh
adautocfg.sh adformsctl.sh adoafmctl.sh adstpall.sh ieo L308827.log mwactlwrpr.sh
$ adautocfg.sh
Enter the APPS user password:
The log file for this session is located at: /d01/app/oracle/inst/apps/PROD_ebs/admin/log/05222339/adconfig.log
AutoConfig is configuring the Applications environment...
AutoConfig will consider the custom templates if present.
Using CONFIG_HOME location : /d01/app/oracle/inst/apps/PROD_ebs
Classpath : /d01/app/oracle/apps/apps_st/comn/java/lib/appsborg2.zip:/d01/app/oracle/apps/apps_st/comn/java/classes
Using Context file : /d01/app/oracle/inst/apps/PROD_ebs/appl/admin/PROD_ebs.xml
Context Value Management will now update the Context file
The log file for this session is located at: /d01/app/oracle/inst/apps/PROD_ebs/admin/log/05222339/adconfig.log
AutoConfig is configuring the Applications environment...
Context Value Management will now update the Context file
Updating Context file...COMPLETED
Attempting upload of Context file and templates to database...COMPLETED
Configuring templates from all of the product tops...
Configuring AD_TOP........COMPLETED
Configuring FND_TOP.......COMPLETED
Configuring ICX_TOP.......COMPLETED
Configuring IEO_TOP.......COMPLETED
Configuring BIS_TOP.......COMPLETED
Configuring AMS_TOP.......COMPLETED
Configuring CCT_TOP.......COMPLETED
Configuring WSH_TOP.......COMPLETED
Configuring CLN_TOP.......COMPLETED
Configuring OKE_TOP.......COMPLETED
Configuring OKL_TOP.......COMPLETED
Configuring OKS_TOP.......COMPLETED
Configuring CSF_TOP.......COMPLETED
Configuring IGS_TOP.......COMPLETED
Configuring IBY_TOP.......COMPLETED
Configuring JTF_TOP.......COMPLETED
Configuring MWA_TOP.......COMPLETED
Configuring CN_TOP........COMPLETED
Configuring CSI_TOP.......COMPLETED
Configuring WIP_TOP.......COMPLETED
Configuring CSE_TOP.......COMPLETED
Configuring EAM_TOP.......COMPLETED
Configuring FTE_TOP.......COMPLETED
Configuring ONT_TOP.......COMPLETED
Configuring AR_TOP........COMPLETED
Configuring AHL_TOP.......COMPLETED
Configuring OZF_TOP.......COMPLETED
Configuring IES_TOP.......COMPLETED
Configuring CSD_TOP.......COMPLETED
Configuring IGC_TOP.......COMPLETED
AutoConfig completed successfully.
[applmgr@ebs scripts]$
Restart Apps R12 EBS middle tier services.
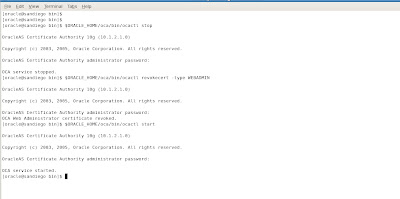
Our final step on the road to SSL for Oracle Release 12 for the E-Business Suite is to stop and restart the middle tier services. We use the adapcctl.sh script located in the $ADMIN_SCRIPTS_HOME directory to stop and restart the middle tier Apache services.
[applmgr@ebs scripts]$ adapcctl.sh stop
You are running adapcctl.sh version 120.6.12000000.2
Stopping OPMN managed Oracle HTTP Server (OHS) instance ...
adapcctl.sh: exiting with status 0
adapcctl.sh: check the logfile /d01/app/oracle/inst/apps/PROD_ebs/logs/appl/admin/log/adapcctl.txt for more information ...
[applmgr@ebs scripts]$ adapcctl.sh start
You are running adapcctl.sh version 120.6.12000000.2
Starting OPMN managed Oracle HTTP Server (OHS) instance ...
adapcctl.sh: exiting with status 0
adapcctl.sh: check the logfile /d01/app/oracle/inst/apps/PROD_ebs/logs/appl/admin/log/adapcctl.txt for more information ...
[applmgr@ebs scripts]$ adapcctl.sh status
You are running adapcctl.sh version 120.6.12000000.2
Checking status of OPMN managed Oracle HTTP Server (OHS) instance ...
Processes in Instance: PROD_ebs.ebs.sandiego.com
-------------------+--------------------+---------+---------
ias-component | process-type | pid | status
-------------------+--------------------+---------+---------
OC4J | oafm | 8269 | Alive
OC4J | forms | 8267 | Alive
OC4J | oacore | 8268 | Alive
HTTP_Server | HTTP_Server | 21490 | Alive
adapcctl.sh: exiting with status 0
adapcctl.sh: check the logfile /d01/app/oracle/inst/apps/PROD_ebs/logs/appl/admin/log/adapcctl.txt for more information ...
There are of course many advanced options for SSL configuration beyond the scope of what we have covered today. I encourage you to dig deeper into the above reference Metalink notes and test to find out what SSL options will benefit your Oracle E-Business Release 12 environments. As you can now see, SSL configuration requires different steps for the E-Business Suite than for a stand alone Oracle 10g Application Server environment. Until next time where we provide some troubleshooting tips on Oracle 10g Application Server.
Cheers,
Ben